Biography
I’m a PhD graduate in Computer Science from Yale, advised by Ruzica Piskac and Jakub Szefer. My current research focuses on training transformers to solve NP-complete problems using reinforcement learning and improving test-time compute strategies for reasoning. My PhD thesis explores learning randomized reductions and program properties (Bitween) for security, privacy, and side-channel resilience.
Currently, I am an Applied Scientist at the Automated Reasoning Group at AWS, where I work on Neuro-Symbolic AI to prevent factual errors caused by LLM hallucinations using mathematically sound Automated Reasoning checks (Amazon Bedrock Guardrails).
During my PhD, I investigated side-channel vulnerabilities in low-level code (EuroS&P 2023) and reverse-engineered quantum circuits from power traces (CHES 2024, CCS 2023). I also explored quantum fault injections and malware (QCE 2024, HOST 2023), analyzed non-functional behaviors of intermittent programs (TECS 2023), developed software countermeasures using randomized reductions (ICCAD 2024), and surveyed security verification techniques (JETC 2023).
Before my PhD, I applied formal methods in industry as a research software engineer through my start-up, contributing to several research collaborations (COMPSAC 2019, FSE 2018, FSE 2017, ASE 2017, SAC 2017).
- Neuro-Symbolic AI
- Automated Reasoning
- Reinforcement Learning
- Machine Learning
- Security & Privacy
PhD in Computer Science, 2025
Yale University, CT, US
MSc, MPhil in Computer Science
Yale University, CT, US
MSc in Information Technologies
Ege University, Izmir, TR
BSc in Computer Science
Dokuz Eylul University, Izmir, TR
Publications
Experience
Research Asistant:
- Member of Rigorous Software Engineering (ROSE) Lab.
- Member of Computer Architecture and Security (CASLAB) Lab.
Teaching Asistant:
- CS437–Database Systems (Avi Silberschatz)
- CS423–Operating System (Avi Silberschatz)
- CS440–Advanced Databases (Robert Soule)
Service
- Action IC1402 - Runtime Verification beyond Monitoring (ARVI)
- Received a short-term scientific mission grant to visit Division of Formal Methods, Chalmers University of Technology, Gothenburg, Sweden,
- Action IC1404 - Multi-Paradigm Modelling for Cyber-Physical Systems (MPM4CPS)
- Received a short-term scientific mission grant to visit Modelling, Simulation and Design lab (MSDL), University of Antwerp, Antwerp, Belgium.
Featured Projects
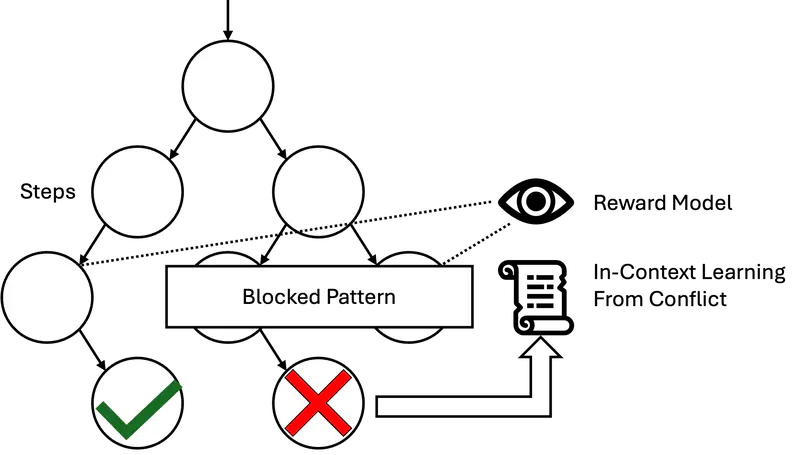
Recent advances in reasoning models have improved performance in logic, mathematics, and programming but struggle with combinatorial reasoning tasks due to the vast search space. Existing neuro-symbolic techniques rely on formal translations and symbolic solvers but are limited and error-prone. We introduce CDCL-IC, a Chain-of-Thought (CoT) reasoning approach leveraging Conflict-Driven Clause Learning (CDCL) to prune search spaces via in-context learning. Applied to Sudoku, CDCL-IC significantly outperforms traditional CoT and o3-mini on 9x9 puzzles.
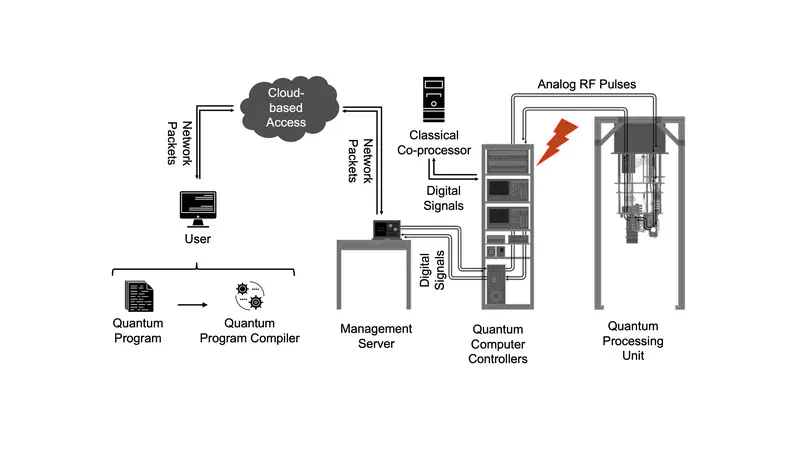
This work shows the first exploration and study of power-based side-channel attacks in quantum computers. The explored attacks could be used to recover information about the control pulses sent to these computers. By analyzing these control pulses, attackers can reverse-engineer the equivalent gate-level description of the circuits, and the algorithms being run, or data hard-coded into the circuits.
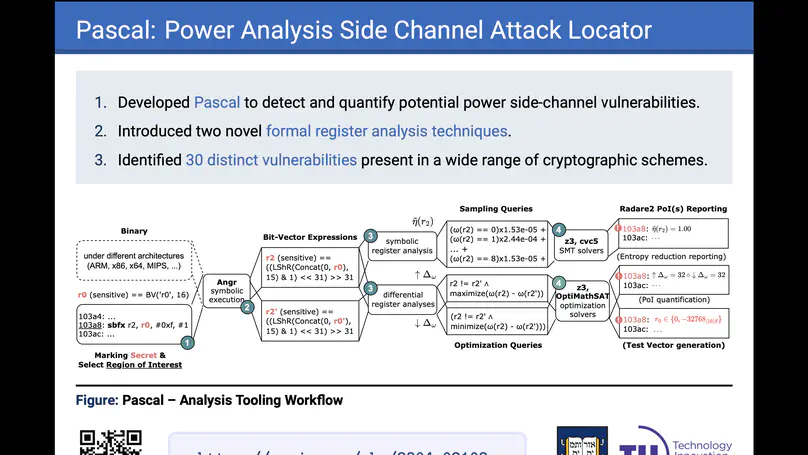
Pascal is a tool that introduces novel symbolic register analysis techniques for constant-time low-level cryptographic code, and verifies locations of potential single-trace power side-channel vulnerabilities with high precision. Pascal is evaluated on a number of implementations of post-quantum cryptographic algorithms, and it is able to find dozens of previously reported single-trace power side-channel vulnerabilities in these algorithms, all in an automated manner.
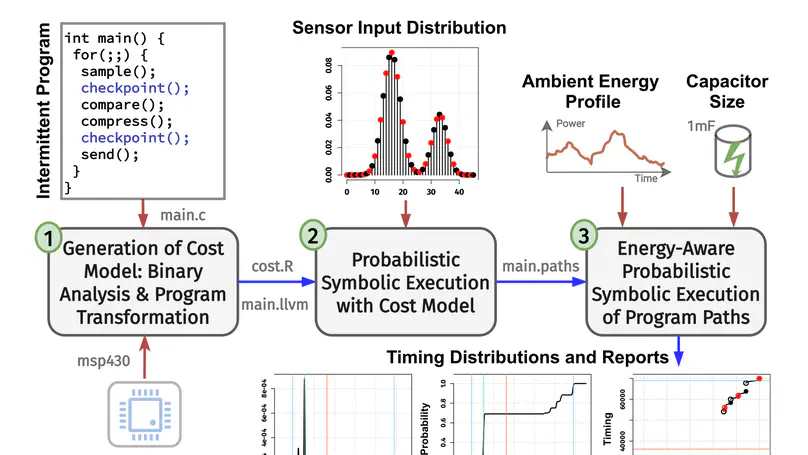
Energy harvesting battery-free embedded devices rely only on ambient energy harvesting that enables stand-alone and sustainable IoT applications. These devices execute programs intermittently when the harvested ambient energy in their energy reservoir is sufficient to operate and stop execution abruptly (and start charging) otherwise. This work presents a probabilistic symbolic execution approach that analyzes the timing and energy behavior of intermittent programs at compile time.
Contact
- ferhat.erata@yale.edu
- 51 Prospect Street, AKW 203, New Haven, CT 06511